Introduction
This Guide is Built on Trust.
J. O’Brien Company is an enterprise level provider of modern security solutions. We educate and collaborate with our clients to solve their security needs, while planning for their future. In business for over 30 years, our experience in access control, credential management, card printing, and custom products has gained us global recognition. As an HID Global Channel Partner we have expert staff to assist our customers strategically to achieve their access control infrastructure goals.
The following guide is intended to provide valuable information to those interested in access control technology. If at any point you find yourself wanting more information, have a question, or would like to speak to an expert, please schedule a free consultation, we are here to help!
SEOS: The Latest and Greatest in Access Technology
What is the latest and gratest in card security? SEOS.
The Seos card platform features AES-128 encryption and best-in-class mutual authentication—an enterprise-grade system that is more secure than most credential technology. As part of the iCLASS SE platform, the high-frequency Seos smart cardsprovide the right combination of strong protection, flexibility, and ease of management.
The History of Access Credential Technology
Access Card Technology Has Come a Long Way
PLAN FOR THE FUTURE BY UNDERSTANDING THE PAST
From lock and key to mobile phones, access control technology has had many reiterations and advancements. Knowing where your current system resides in the progression of the access control timeline is essential to making informed decisions for the future. Understanding your current card, reader, controller, and software infrastructure will assist your security team in adopting the latest and greatest in access technology.
1980s — Swipe Technologies
1990s – “Prox”
Late 1990s-2010s — First-Generation Contactless Smart Cards
2013-Present — Second-Generation Contactless Smart Cards
The Next Generation of Credentials — Mobile Devices
How Does an Access Control System Work?
The Security Within the Components of an Access control system Dictate Risk
Know what you are working with
Four elements common to all access control solutions – and how they interact
The Credential
Physical access credentials come in a variety of form factors – Smart Card, fob, mobile device and others. They almost all carry a number, or set of numbers, that are used to identify the card holder – usually a simple string of binary numbers (ones and zeros) often referred to as the payload. The way data is conveyed to the reader varies according to the technology involved. The way the data is configured is called the format.
Common credential technologies include:
- Magnetic Stripe (Legacy Technology)
- Magnetic Stripe (Legacy Technology)
- High Frequency 13.56MHz (Current standard)
- Ultra High Frequency
The Reader
Some readers are designed to support just one technology, while others support an array of multi-technology configurations. The reader itself has no awareness of the makeup of the card data format, nor is it aware of any access privileges for the cardholder.
The Controller
The controller is the only device in the system where the binary credential data format can be decoded and acted upon. When the controller receives the data from the reader, embedded firmware decides whether, or not to grant access.
The Software
Every access control system has some form of user interface, usually a discrete PC application or web-based interface for operators to interact with the system. They will use it to:
- Add and delete cardholders
- Assign, modify or delete access privileges
- Create and modify time schedules, holiday lists, etc.
- Configure system hardware for doors, alarm points, etc.
- Monitor system events in real time
- Generate historical reports on all types of system activity
In most cases the access system is fully automated and connected to the reader and door hardware via dedicated wiring.
Proximity Cards: Unsecure and Outdated
A LACK OF SECURITY
Proximity cards lack the security that you can achieve with other access control solutions. The low-frequency (125Khz) of the technology leaves a gaping hole for hackers and identity thieves to steal the unencrypted information. All they need is an inexpensive card reader/writer to steal the credentials and create a duplicate card. Your identity and access codes become available to anyone in close proximity of the proximity card. Your security system is then tracking an intruder under the guise of an authorized employee or visitor. You don’t “see” who’s accessing your facility, so your security is compromised.
A NEW GENERATION OF CARDS
We’re now in the second generation of contactless smart cards, a technology that has evolved from proximity cards. The low frequency of the early proximity cards has risen to a standard of 13.56Mhz. Today’s contactless smart cards also store more data than the proximity cards, and with much higher security protocols.
Reasons To Upgrade Your Access Control System
Your company’s security needs are constantly evolving, which can result in an upgrade to your physical access control system. The following list outlines the various driving factors that could justify an access control upgrade:
- Your company merges or acquires another company.
As your company begins a merger or an acquisition, it can be costly to integrate two different legacy systems. - You need a common system standard for multiple locations.
Managing multiple company locations with different security systems is a challenging process. - Your organization is consolidating, adding locations or relocating.
This may require an entire mass re-badge. - Your brand image or logo changes.
A re-brand of your organization results in a change of security cards. - Your company needs to incorporate new, innovative card applications to meet employee needs.
An outdated system can pose risks for your employees. - Your company needs to minimize risk by upgrading an outdated system.
An outdated system can pose risks for your employees. - Your security requirements change.
New regulatory requirements can force your company to make security changes. - You have a breach in security or a security event occurs.
Older security systems are subject to breaches.
Read the full article on 8 Reasons to Upgrade your Access Control System
Need advice on how to upgrade? We offer free support.
Technologies that Support Mobile Credentials
WHAT ARE THE CURRENT TECHNOLOGIES THAT SUPPORT MOBILE ACCESS?
1) Near Field Communication (NFC)
Until recently, the only way to enable mobile credentials on a mobile phone was by creating a Secure Element, such as a Sim Card. In 2014, Google released a new NFC feature called Host-Based Card Emulation. Rather than having a secure element, the new NFC feature allows the contactless card to be hosted in an app. Now, it is possible to use standard based card technology with NFC readers to use mobile credentials.
Cons with this technology: Currently, this technology is not supported by IPhone.
2) Bluetooth Smart
Bluetooth Smart is the best option available for mobile credentials. Bluetooth Smart is supported on both Android and Bluetooth systems. Additionally, Bluetooth smart has a low power consumption, there is no pairing needed, and can support long range distances. This will allow you to place the readers in a safe location or hidden location.
An Overview of HID® Mobile Access
ACCESS CONTROL IN A MOBILE FIRST WORLD
It is a Mobile World.
From smartphones to wearable and tablets, mobile devices are ever present in today’s work environment, always on hand, serving a variety of purposes. Mobile has become the go-to technology of the new millennium, offering convenience and portability. Leveraging mobile technology to access doors, parking facilities and gates – not to mention networks and other enterprise applications and much more – is a logical step in the evolution of access control.
Mobile Access by HID Global Allows for:
1. UNPRECEDENTED SECURITY AND PRIVACY PROTECTION OF IDENTITY DATA
The Seos card platform features AES-128 encryption and best-in-class mutual authentication—an enterprise-grade system that is more secure than most credential technology. As part of the iCLASS SE platform, the high-frequency Seos smart cardsprovide the right combination of strong protection, flexibility, and ease of management.
2. ULTIMATE CONVENIENCE FOR YOUR EMPLOYEES
The same mobile device you use to open gates and doors, can allow you to log on to the network, open electronic locks and securely release documents from the printer. You can also use this same device for time and attendance, to get a snack from the vending machine
3. EFFICIENT USER MANAGEMENT
Efficiently deploy and manage mobile users with HID’s Mobile Access Portal and App. HID Mobile Access provides superior identity management with the most dynamic and complete mobile solution available today. Mobile-enabled readers, secure mobile IDs, cloud-based management portal – all built to work together, seamlessly.
Components of HID® Mobile Access
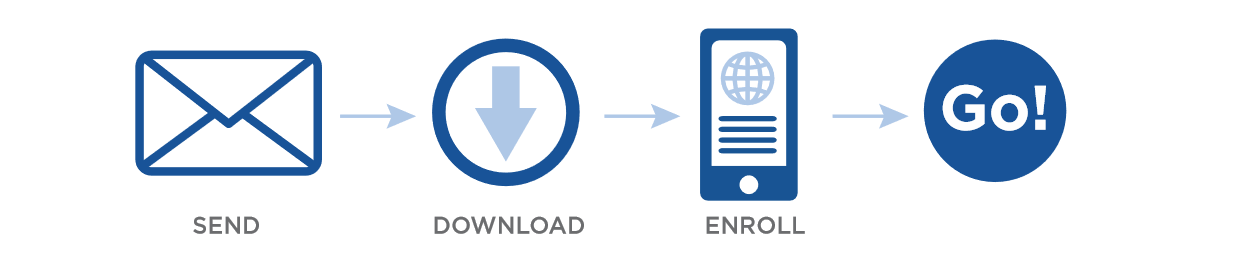
HID Mobile Access® complements existing access control systems. Besides using cards or fobs, your staff can now securely access the facility using their Android or iOS mobile device. HID Mobile Access, powered by Seos® consists of four simple components.
- HID Mobile Access Reader: iCLASS SE® or multiCLASS SE® mobile-enabled readers
- HID Mobile Access Management Portal: A management portal that allows you to manage users and securely issue or revoke Mobile IDs to users’ handsets
- Mobile IDs: The Mobile IDs with integrated Seos technology are for management of trusted identities
- HID Mobile Access Application: This app is for Android and iOS devices
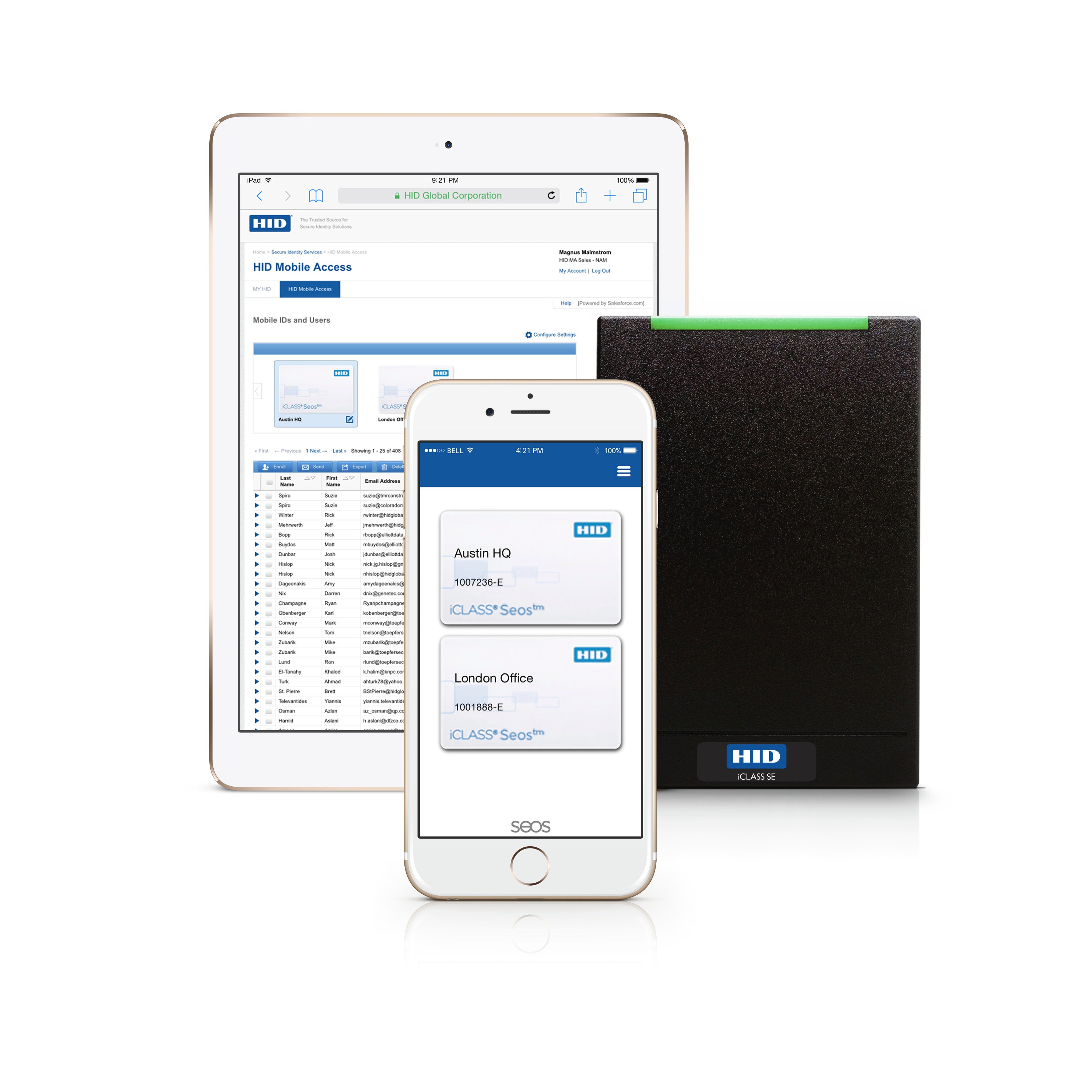
HID Mobile Access Readers
A familiar appliance recognized by almost all the working world, HID iCLASS SE Mobile Access Readers are physical access wall mounted readers read Mobile IDs – the virtual credentials on mobile devices. They also read contactless credentials. The reader securely reads a physical access card.
HID Mobile Access Management Portal
The HID Mobile Access application within HID Global’s Secure Identity Services Portal, allows enterprise administrators to manage users and issue and revoke Mobile IDs to user’s mobile devices. The portal is a hosted service available to registered users via a web link. Each enterprise has its own secure portal, which is set up by HID Global during the On-boarding Process.
Mobile Access Application
The HID Mobile Access Application manages the Mobile IDs and contains some limited user settings. Users can download the free HID Mobile Access Application free of charge for Android mobile devices via Play Store and for iOS devices via the Apple App store after the Portal Administrator enrolls the new users via the portal.
Benefits of HID® Mobile Access
Mobile Access is creating a wave of convenience that is sweeping through the world of secure access. Mobile Access from HID Global, allows users to access secure doors, parking, networks and more by using their mobile device rather than a physical card. No more lost cards to replace, no scrambling when you’ve left your card at home. But convenience is just the beginning. Mobile access brings a wealth of benefits for managing secure access.
Benefit #1: Sustainability
With secure ID information in your mobile device you initiate the reduction of the vast plastic card population. Without a physical item to produce and ship, the carbon footprint of your identification program is drastically reduced. Plastic ID cards also typically feature other plastic accessories such as lanyards, badge holders, and clips.
Benefit #3: Innovative
While the Seos technology that powers Mobile Access is truly innovative, in the world of technology there is always a little one-upmanship when it comes to getting the latest and greatest. The ability to impress clients (and friends) with cutting edge technology is a real plus. Being an early adopter confers status as an innovator. Many users consider their smartphone/tablet to be their technological bag of tricks with virtually unlimited potential and they’re eager to add useful functionality to their arsenal.
Benefit #4: Ease of Use
Instantly issue or revoke a Mobile ID. Mobile IDs can easily be issued to workers remotely – no need for face to face interaction. Users just download the app and their unique ID code. Rather than managing an inventory of physical keys, management is at your fingertips, in an easy to use digital dashboard. When a user, say a contractor, no longer requires access, their ID is simply deactivated – eliminating the cumbersome need to turn in a physical card.
Benefit #5: Security
People lose their mobile phones far less frequently than plastic cards. And Mobile IDs can be further protected by using phone security feature such as a PIN. Lost cards are no longer a problem. And a smartphone is much less likely to be “shared,” or loaned to someone else. Would you lend your smart phone to someone else for the day?



.png?width=580&name=Progression%20of%20access%20control%20(cropped).png)



/Mobile%20Credentials/NFC.png?width=721&name=NFC.png)
/Mobile%20Credentials/bluetooth.png?width=1280&name=bluetooth.png)